Zyxel statement to vulnerability CVE-2017-3216
A recently uncovered vulnerability identified in US-CERT vulnerability note VU#350135 and CVE Advisory CVE-2017-3216 exposes a security weakness in the web-based administration interface of Zyxel WiMAX Client Premise Equipment (CPE). The vulnerability could allow an unauthenticated attacker to change the administrator password on the device.
Zyxel has conducted a thorough investigation and is now working on the solutions for the susceptible models, as listed in Table 1.
Workarounds
Zyxel suggests users of the susceptible devices disable WAN device management function following the steps below:
- Log in the web-based management interface of the device
- Click “Maintenance” and “Remote MGMT”
- Disable (unclick) “HTTP and HTTPs – allow connection from WAN”
- Save the setting
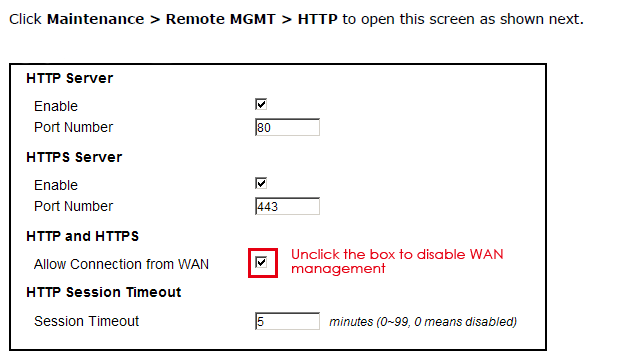
Table 1. Susceptible models
| Product | Model name | Fix schedule |
|---|---|---|
| WiMAX CPE | MAX218M | June 16 2017 |
| MAX218M1W | June 23 2017 | |
| MAX218MW | June 30 2017 | |
| MAX308M | July 7 2017 | |
| MAX318M | July 14 2017 | |
| MAX338M | July 21 2017 |
Please contact your local service representative if you require further information or assistance. To report a security vulnerability, please contact security@zyxel.com.tw
