
Uncompromising and Unifying Network Protection
View AwardsThe Zyxel ZyWALL ATP series is an Advanced Threat Protection Firewall dedicated to small and medium businesses, empowered by cloud intelligence leveling up network protection, especially in tackling unknown threats. The series does not only support all Zyxel security services such as Web Filtering, Application Patrol, Anti-Malware, Reputation Filter, etc. but also Sandboxing and SecuReporter. An infographic dashboard is also included, delivering high performance and ensuring comprehensive protection as a self-evolving solution.
Try DemoElevate Collaboration
with Advanced ATP on Cloud
To power network security, we strengthen the Zyxel Security Matrix in Nebula with ATP firewalls on cloud, giving peace of mind with collaborative network defense and sandboxing provisioning. Get detailed reports for investigations, active monitoring, high visibility of network activities, with our evolving security protection.

Comprehensive Threat
Detection and Prevention
ATP firewall is equipped with multiple protection tools such as Sandboxing to stop unknown malware and zero-day threats, and CDR can block or quarantine the compromised clients at the network edge, containing the threat and preventing further damages. It simplifies the protection of all your business networks without worries.

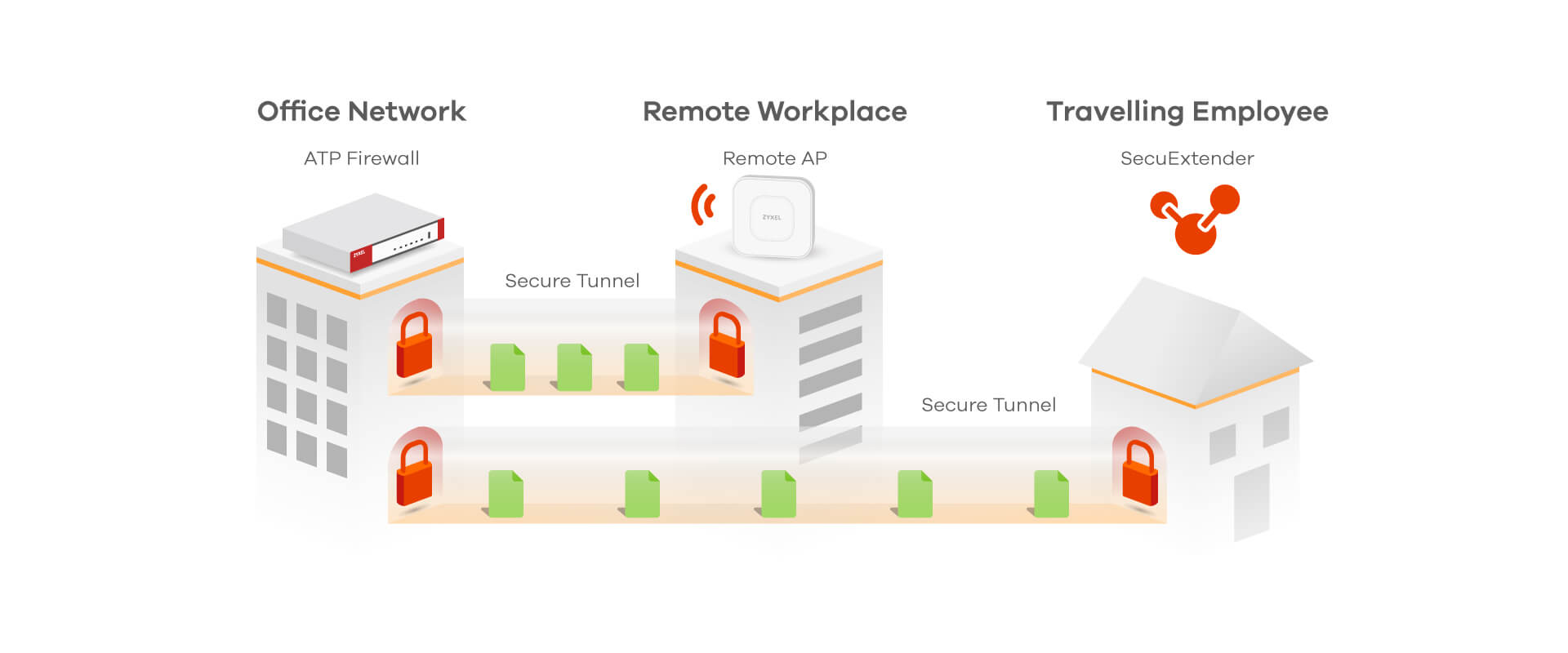
Same Security Across Networks
We offer a wide array of products that allow different remote access options including firewalls for headquarters and branch offices, remote access points with Secure WiFi and VPN client for off-site employees, extending endpoint protection.
Increasing Visibility to
Optimize Resource Usage
ATP can help business to manage what applications the employees are using and quickly see all the applications at a glance. More than 3,700 applications are categorized into different labels. Simply hover to block or unblock any one of them. It’s that simple for application monitor and management.
Just Connect with Nebula
Resellers, Managed Service Providers (MSPs) and network Administrators will find Simplicity, Scalability, Flexibility, reduced IT risk and reduced costs through Zyxel’s Cloud Networking Management platform, Nebula a single-vendor approach.
Nebula offers powerful, effortless and scalable network connectivity that works together to remove the complexity and security risks often associated with having a mixed vendor approach to networking.
Connect, protect and manage Security, Switch, Wireless and LTE/5G connectivity via our centralized Cloud platform, Nebula.
Serving customers with over 80 Nebula enabled devices via an ever-growing portfolio, Zyxel is unmatched in its approach to onboarding new and existing products via NebulaFlex. From Deploying a home office to delivering connectivity to distributed network configurations, Zyxel’s Portfolio of Nebula enabled products can accommodate all types of budgets, functionality and scalability for now and for the future.




