Applications for the Multy Device
The Multy Device supports the following applications.
Guest WiFi
The Multy Device allows you to set up a guest WiFi network where users can access the Internet through Multy Device, but not to other networks connected to it.
OpenVPN Server/Client
OpenVPN is a VPN protocol which is open source and free of charge. It can be used to create a virtual private network or to connect local networks. See Differences Between Multy Devices for more information on the Multy Device models that support OpenVPN.
OpenVPN Server Network Scenario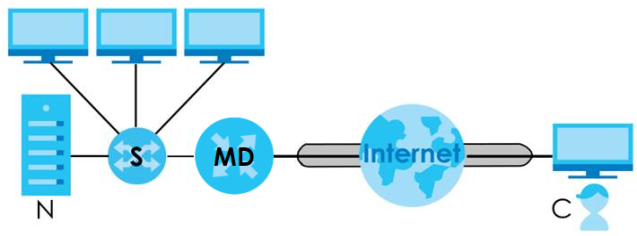

The labels used in the graphic are explained below:
• C – A client device connected to the OpenVPN server. Make sure to install OpenVPN client software on the client device first.
• MD – A Multy Device that serves as the OpenVPN server.
• S – A switch that connects the Multy Device and the local network.
• N – A local network behind the OpenVPN sever.
OpenVPN Client Network Scenario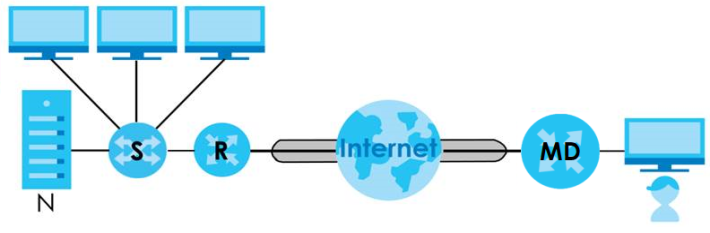

The labels used in the graphic are explained below:
• MD – A Multy Device that serves as the OpenVPN client.
• R – A router that serves as the OpenVPN server.
• S – A switch that connects the OpenVPN server and the local network.
• N – A local network behind the OpenVPN sever.
IPv6 and IPv6 Firewall
IPv6 (Internet Protocol version 6), is designed to enhance IP address size and features. The increase in IPv6 address size to 128 bits (from the 32-bit IPv4 address) allows up to 3.4 x 1038 IP addresses. The Multy Device can use IPv4/IPv6 dual stack to connect to IPv4 and IPv6 networks, and support IPv6 rapid deployment (6RD).
Consequently, you can enable and create IPv6 firewall rules to filter IPv6 traffic.
Firewall protects your Multy Device (MD) and network from attacks by hackers on the Internet and control access to it. The firewall:
• allows traffic that originates from your LAN computers to go to all other networks
• blocks traffic that originates on other networks from going to the LAN.
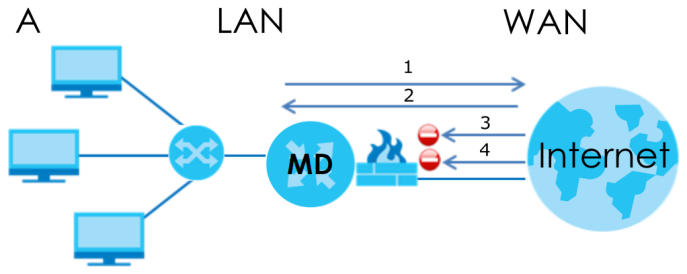
The following figure illustrates the firewall action. User A can initiate an IM (Instant Messaging) session from the LAN to the WAN (1). Return traffic for this session is also allowed (2). However other traffic initiated from the WAN is blocked (3 and 4).
Default Firewall Action